How To Register Arch In Google Authenticator
In this guide, nosotros are going to learn what is Multi-Factor hallmark and its importance and finally how to setup Multi-Gene authentication for SSH in Linux using Google Authenticator app.
Introduction
Security is a serious business concern. The number of compromises is significantly growing 24-hour interval past solar day and it is estimated that by 2025 cybercrime will crusade companies 10.5 trillion USD.
Information technology is important that a strong layer of security exist implemented across all layers of the engineering stack. In this commodity, nosotros are going to run into one such security implementation for ssh using multi-cistron authentication.
SSH, stands for Secure Shell, is a network protocol that allows users to connect to the remote machines (servers) and access resources.
The ssh protocol implements two types of security namely Countersign-based authentication, and Fundamental-based authentication.
Central-based (public -> private) hallmark is considered more than secure compared to countersign-based authentication and nigh SSH hardening instructions recommended disabling password-based authentication and enabling only key-based authentication.
Irrespective of what hallmark machinery you choose, you lot can make ssh more than secure by implementing a multi-factor authentication setup.
What is Multi-Factor Authentication?
Mutli-factor authentication (shortly MFA) is a secure process of authentication which requires more than than one authentication technique chosen from independent categories of credentials.
Multi-Gene Authentication is besides sometimes called as "Two-cistron authentication (2FA)".
There are two factors involved in validating who you lot say you are. The first gene will be the password that is created when your user account is created.
The second cistron volition exist any awarding that generates OTP or any protocol that sends you text letters or make a phone call to your device.
Depending upon how the application is implemented the way you authenticate vary. Some common tools you use for MFA are:
- Application installed on the mobile device that generates tokens.
- An external device like Yubikey.
- Fingerprint.
- Facial recognition.
- Text Bulletin or call-in based OTP countersign.
To enable multi-factor authentication for ssh we volition be using "Google Authenticator" app which uses the Oath-TOTP protocol. There are other alternative tools like Twilio Authy or FreeOTP which you lot tin install and endeavor out.
We will outset with installing the Google Authenticator app on both the server and mobile device and try to enable MFA and validate.
Install Google Authenticator
Offset Install the Google Authenticator app on your Android or IOS devices through the playstore/Itunes.

Now, install Google Authenticator app on your Linux system.
Depending upon your distribution, run the following installation commands.
In Ubuntu and its derivative distributions run the post-obit command.
$ sudo apt install libpam-google-authenticator
In RHEL based distributions run the following command.
$ sudo dnf install google-authenticator -y
For Curvation based distribution run the following command.
$ sudo pacman -S libpam-google-authenticator
Generate Initial Token For A User
As the kickoff step in setting up MFA, yous accept to run the following command from your terminal. This volition accept care of the initial setup by generating the TOTP key. This cardinal is for the user who is running the control and is not applicable to all users in the system.
$ google-authenticator
In that location are some sequence of steps where you will be prompted with the (y/n) option.
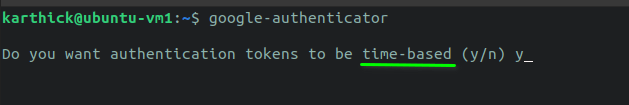
Pace 1 - It will prompt you to cull fourth dimension-based authentication tokens. Time-based authentication tokens will generate a new code every 30 seconds. Printing "y" to continue.
STEP 2 - Underground token will exist generated along with a QR lawmaking. Open the Google Authenticator mobile app and scan the QR code or manually type the hush-hush key to register the device. Once it is done, now the app volition start generating tokens every 30 seconds.

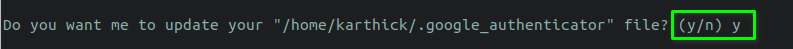
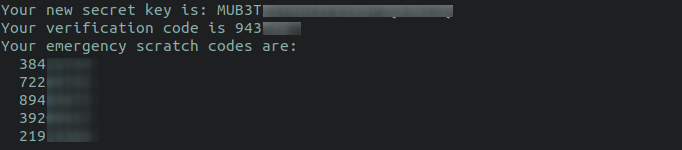
STEP iii - In this pace, it will prompt you to update the .google_authenticator file nether your habitation directory. All the secret keys, verification code, emergency scratch codes are saved in this file. Press "y" to keep.
Step 4 - Choosing "y" in this step will expire the token immediately once yous take used it to cosign. In this instance, even if some hackers get your token, it will be expired.
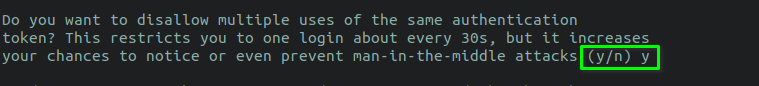
STEP 5 - This pace decides how many tokens volition be allowed and the time frame. When I choose "northward", information technology volition allow for 3 tokens in a 90 seconds window. If I printing "y", information technology volition let 17 tokens in a 240 seconds fourth dimension window.
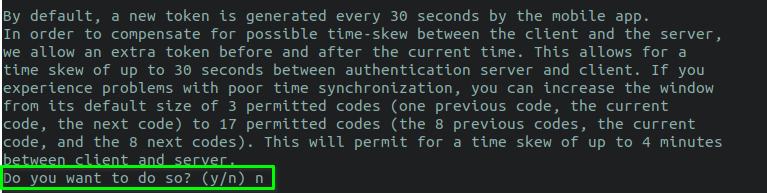
STEP 6 - This step will ask yous to enable rate-limiting. Rate limiting allows an assailant to try merely 3 login attempts every thirty seconds. If the tokens are incorrect then they accept to await for Due north time to try again.

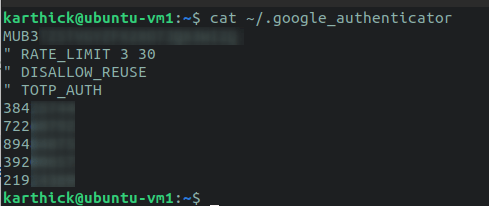
Nosotros have completed the first step. Open the file ~/.google_authenticator and you can find all the settings and secret codes we fabricated through all these steps.
$ cat ~/.google_authenticator
You can also laissez passer arguments to the google-authenticator command which will create the keys and other settings without going through this sequence of steps.
$ google-authenticator -q -t -d -f -r iii -R thirty -w 3
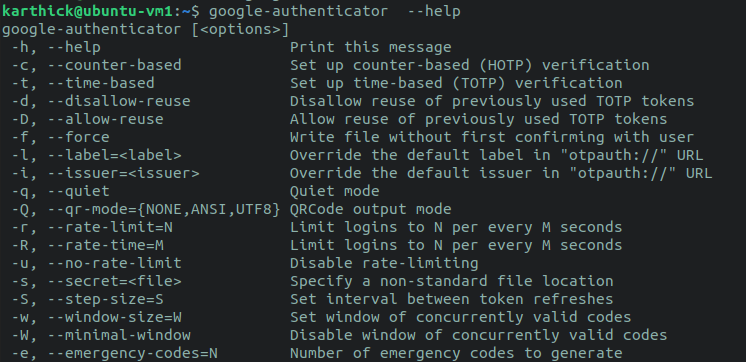
Refer the Google authenticator assistance section to find what those arguments volition do.
$ google-authenticator –-assistance
Configure SSH For Multi-Factor Authentication
We have to brand some configuration changes to openSSH and then nosotros tin can commencement using MFA.
Note:
- As a all-time practice, e'er backup your configuration files before making whatever changes. If annihilation is messed up the changes can be reverted.
- Since you are making changes to SSH configuration files, make certain you accept a session opened separately, so yous are non going to be locked out of yourself by accidentally.
Run the following commands to back up the SSH config files.
$ sudo cp /etc/ssh/sshd_config /etc/ssh/sshd_config.backup
$ sudo cp /etc/pam.d/sshd /etc/pam.d/sshd.backup
Beginning, enable SSH to use MFA past setting ChallengeResponseAuthentication selection to "yes".

Next, edit the /etc/pam.d/sshd file:
$ sudo vi /etc/pam.d/sshd
And add the post-obit lines to the bottom of the file.
auth required pam_google_authenticator.so nullok auth required pam_permit.so
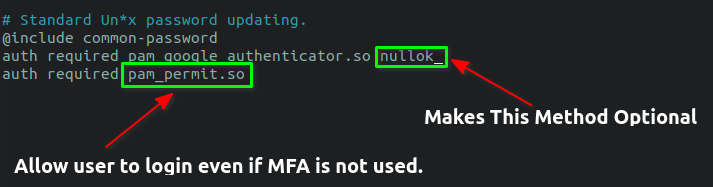
If you lot wish to make MFA mandatory for all users, and so remove the word "nullok".
Restart the ssh service to brand the changes constructive.
$ sudo systemctl restart sshd
Test Two Factor Authentication
It's fourth dimension to examination if the changes we made are effective.
Connect to the server via SSH and you volition exist asked for a countersign equally the first gene followed past a verification code as the 2nd-factor authentication as shown in the below prototype.
$ ssh [email protected]/IPaddress
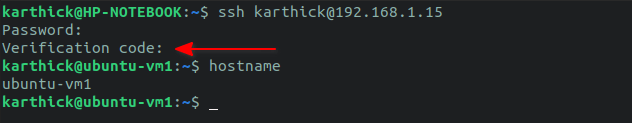
One time you entered the SSH password and the verification code, y'all volition able to login.
Did you recall that we accept not enabled MFA as mandatory for all users? Allow's exam it and see if I am able to connect with another user where I practice not accept generated and prepare tokens.
I have a testuser and I am able to connect successfully without prompting for verification lawmaking.
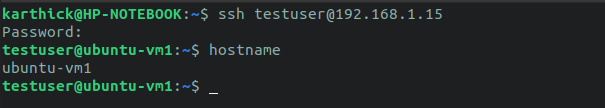
See? I can able to login without the verification code equally well.
Multi-Factor Hallmark For Key Based Authentication
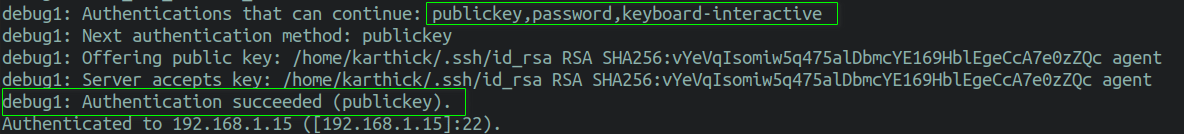
If you have fix a central-based authentication, and then yous will non be promoted for the password or verification codes. Why?
Because, by default ssh uses public-fundamental authentication beginning and if there is a key found then it authenticates using that. In case the key is non plant, it will use password-based hallmark.
Y'all tin use verbose mode to check this.
$ ssh -v [email protected]/IPaddress ## With verbose
Add together the following line to the bottom /etc/ssh/sshd_config file:
AuthenticationMethods publickey,password publickey,keyboard-interactive
Next open /etc/pam.d/sshd and comment out the following line.
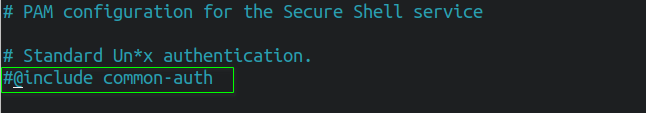
If you lot are non commenting out "@include common-auth" , then it will enable more 2 factors to authenticate. It will first authenticate using keys followed by password and tokens. All I need is a central and token for my hallmark, and so I am disabling it.

Restart the sshd service and test out if the changes piece of work fine.
$ sudo systemctl restart sshd
At present If I endeavor to connect, it uses public-primal as the showtime factor and verification lawmaking as the 2nd factor to authenticate.
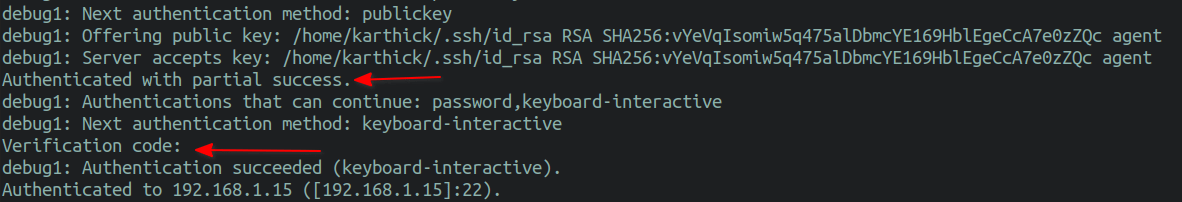
Recovery Steps
There may be scenarios where you may lose or change your mobile device. In that case, you accept to reinstall the google-authenticator awarding and annals the underground key to start generating tokens.
If you are locked out of the organisation, then y'all have to accomplish out to your arrangement administrator to provide you with new secret keys to register and use it. But there is an culling approach where you can log in and generate keys on your own.
Call up the codes that are generated during the initial step? You lot can employ the emergency scratch code equally a token to log in. Each scratch code can be used only in one case. Salve information technology someplace rubber and so it can be used when needed the about.
The codes are saved in ~/.google_authenticator file.
$ cat ~/.google_authenticator
You can now regenerate your own keys once again by running the post-obit command.
$ google-authenticator
Decision
In this article, I accept shown you how to install google authenticator and enable Multi-factor Authentication for SSH with different configurations.
Every bit an ambassador, you can also write bash scripts to automate the procedure of generating the undercover keys and share it with the user. Yous should as well harden the ssh before setting up MFA, so your organization is more than secure. We are planning to encompass them in carve up articles. Stay tuned!
Related Read:
- How To Configure SSH Cardinal-based Authentication In Linux
- Discover If A User Is Using Password-based Or Key-based SSH Authentication
- How To Permit Or Deny SSH Admission To A Particular User Or Group In Linux
- Disable SSH Countersign Authentication For Specific User Or Group
How To Register Arch In Google Authenticator,
Source: https://ostechnix.com/setup-multi-factor-authentication-for-ssh-in-linux/
Posted by: carrawayenticippace.blogspot.com


0 Response to "How To Register Arch In Google Authenticator"
Post a Comment